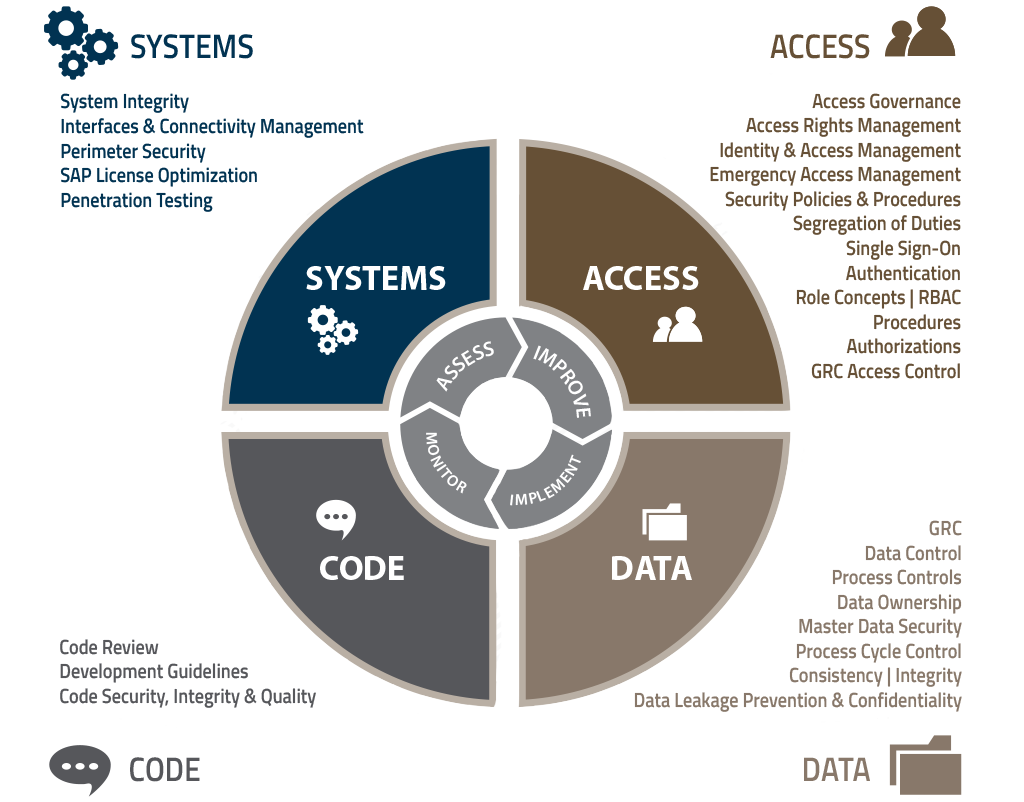
Infrastructure Security
SAP security is not only about Segregation of Duties (SoD) and user access rights, but also the layer below application security, being the infrastructure and kernel security.
Since systems are more and more interconnected, the security on communication layer as well as on kernel level, has become one of the top security priorities. It’s all about keeping the bad guy out to avoid risk of sabotage, fraud or other cyberattacks.
Infrastructure vulnerability analysis helps with identifying security weaknesses on the layer below application security. Generally speaking, infrastructure management and SAP system administration are two different worlds and there tends to be a gap of knowledge and ownership between the two.
The technical foundation of system reliability is assessed through the infrastructure vulnerability analysis. A SAP security specialist should inspect the vulnerability of the installed SAP components, kernel and services for any (known) weaknesses.