- Details
-
Category: Services
Advisory & Consultancy
axl & trax delivers advisory and consultancy services to help companies with facing various and complex security challenges related to their SAP environment. Our advisory & consultancy services cover:
- development of corporate SAP security strategies;
- long range planning in SAP security (e.g. program management, maturity management, defense-in-depth);
- enterprise changing environment: extension, reorganization or rationalization of SAP security technical & management processes in accordance with the enterprise evolution, e.g. multiple stakeholders accessing the enterprise SAP systems, geographical extension, mergers & acquisitions, outsourcing, etc;
- compliance - information & privacy regulation, SoX, JSoX, etc;
- R&D, advice, design and integration of tailored and custom solutions;
- quality assurance.
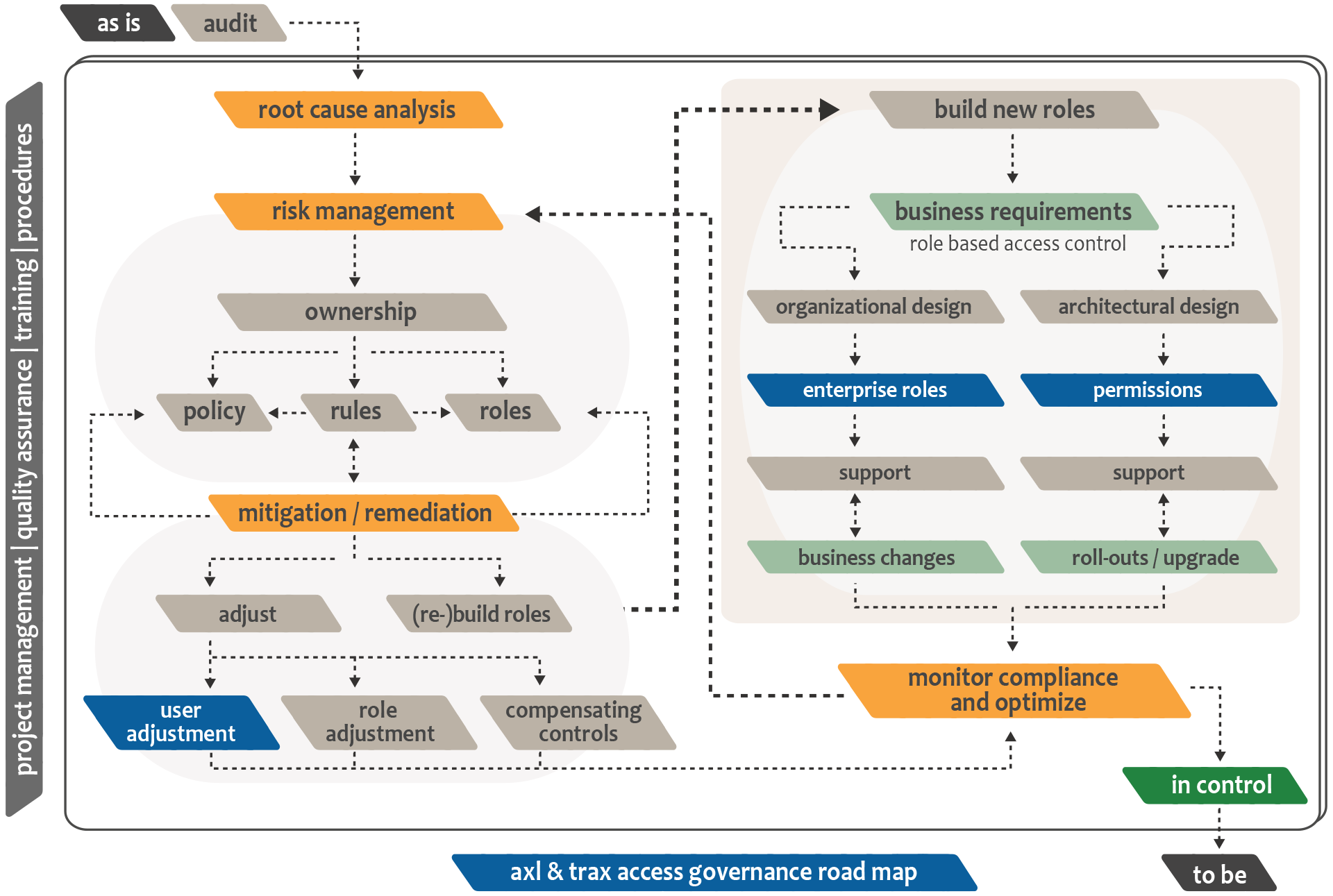
Audit
In order to understand the current security posture or risk exposure, axl & trax performs at-request reviews and audits. The services range from in-depth analysis on SAP security and controls, to high-level assessments - on tactical, conceptual and/or technical level.
We are specialized in SAP audits and have strong experience in auditing user access rights, security role concepts, segregation of duties, business process controls, GRC rule sets and any related SAP security area.
Support
Established security must be maintained to ensure a sustainable protection for valuable information assets. axl & trax helps companies with administering and maintaining their SAP security on a day-to-day basis or for a short period in time e.g. when in-house administrators are ill or on vacation.
Your security support can also be fully or partially outsourced through our Security Operations Center.
Training
axl & trax is a recognized training provider for security, audit, control and GRC within SAP applications and SAP security tools such as SAP GRC, CSI tools and more.
In addition to regularly held open-class and on-site/online training, "à la carte" trainings can be organized for specific topic requests. axl & trax also regularly schedules webinars on SAP security for you to attend from your own computer.